2008 Oct 18
| Low Tech | Whois Databases |
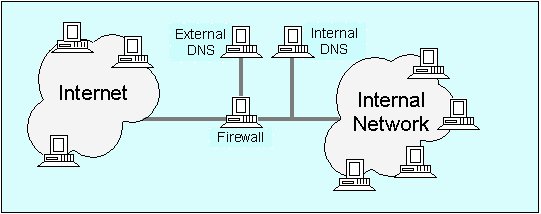
| Social Engineering | DNS Reconnaissance & Defense |
| Web Search | General Reconnaissance Tools |
| Usenet | Web Based Reconnaissance Tools |
These low-tech techniques can possibly learn passwords, learn about network architecture, get system documentation, and even highly confidential information.
Calling an employee at target organizationon the phone and tricking the individual to revealing sensitive information. This can be done by pretending to be another employee, a customer, or supplier. A pretext is used such as being a new employee, administrative assistant, manager or system administrator. Such call can try to get a contact name and number, a sensitive document, or even a password. Examples include: an angry manager calling help desk because their password stopped working, a system administrator needing a user's password to fix their account, a sales person in field needing contact information, getting a voice mail account inside organization (others will trust such a number to leave info).
Physical breakin-in can give access to to much, such as: access to internal net (CAT5 plug or wireless) inside firewall, finding a computer already logged into, sensitive trash and dumpster diving, unlocked file cabinets, removing a hard drive or whole computer. Use a shredder!
Public domain information on the web can include: domain names, network addresses, contact information (names, phone numbers, email), finding dial-in modems, clues about the corporate culture and language, product offerings, work locations, business partners, recent mergers and acquisitions, technologies in use (e.e. Win NT, Oracle database), and much more.
Search engines can find historical information about an organization, and competitors, products, employees, business partners, technologies, current history, and financial status. By searching (e.g. on www.altavista.com) for "link:www.company.com" all web sites that link to the target web site (e.g. vendors and business partners).
Be sure your web site(s) do not reveal what products you use in your environment and their configuration.
Many times eployess wil lanswer detailed quetions here revealing sensitive information on a large scale. Sometimes an employee will ask a detailed question to technical newsgroups about how to configure a particular type of system or troubleshoot a problem. An attacker could send a response with wrong advice which would lower the security of the system. Use the Google newsgroup Web search engine at groups.google.com (which is the acquired DejaNews Web site).
Employess must be trained to not reveal sensitive information on usenet. Make usenet searches to verify this has been done.
The Internet Corporation for Assigned Names and Numbers (ICANN) has an accreditation process for name/number/DNS registrars (such as Network Solutions).
This information is useful to notify someone if their systems are being compromised and used to attack you.
| Type | Type Value |
Sites or Meaning |
|---|---|---|
| Registrars | accredited | www.internic.net/alpha.html |
| Domain | .com .net .org |
InterNIC whois database |
| Domain | .edu | www.networksolutions.com |
| Domain | .gov | whois.nic.gov |
| Domain | .mil | whois.nic.mil |
| Domain | country codes | Allwhois |
| Misc | NIC Handle Name Company Name Host or Nameserver name |
Network Solutions |
| IP Address | In North and South America, Caribbean, Africa |
ARIN :
American Registry for Internet Numbers Network Solutions |
| In Europe | RIPE NCC : Reseaxus IP Europeens Network Coordination Centre | |
| In Asia | APNIC : Asia Pacific Network Information Center | |
| DNS Records |
Address (A record) |
Maps a domain name to an IP address |
| Host Information (HINFO record) |
Identifies associated host system type (e.g. Solaris8) | |
| Mail Exchange (MX record) |
Identifies mail system accepting mail for domain | |
| Name Server (NS record) |
Identifies DNS servers for domain | |
| Text (TXT record) |
Associates an arbitrray text string with domain |
Once a DNS server is known it can be queried using nslookup a program found in Windows NT/2000 and Unix/Linux. First step is a zone transfer, which aks the name server to send all information it has about a domain.
nslookup > server [target_DNS_server name or IP] specify DNS server > set type=any look for any records > ls -d [target_domain] requests information
Other DNS reconnaissance tools include:

| Tool | Functionality |
|---|---|
| Ping | Sends and ICMP Echo Request message to a host to see how fast or if it will respond |
| Whois | Conducts whois lookups uding default whois servers, or by allowing user to specify which whois database to use. |
| IP Block Whois |
Determines who owns a particular set of iP address using ARIN databases. |
| Nslookup | Queries a DNS server to find domain name to IP address mapping. |
| Dig | For getting detailed DNS info about a system. |
| DNS Zone Transfer |
Transfers all information about a domain from prper server. |
| Tracerout | Returns a list of router hops between the source machine and destination. |
| Finger | Queries a system to determine its user list. |
| SMTP VRFY | Determines whether a particular email is valid at a given email server (based on SMTP). |
| Web Browser | A mini Web browser lets the user view raw HTTP interactions. |
| Suite | System | Cost |
|---|---|---|
| Sam Spade | Windows | Freeware |
| CyberKit | Windows | Freeware |
| NetScan | Windows | $25 |
| iNetTools | Windows Mac |
$??? |
2005-2008